6.8 KiB
6.8 KiB
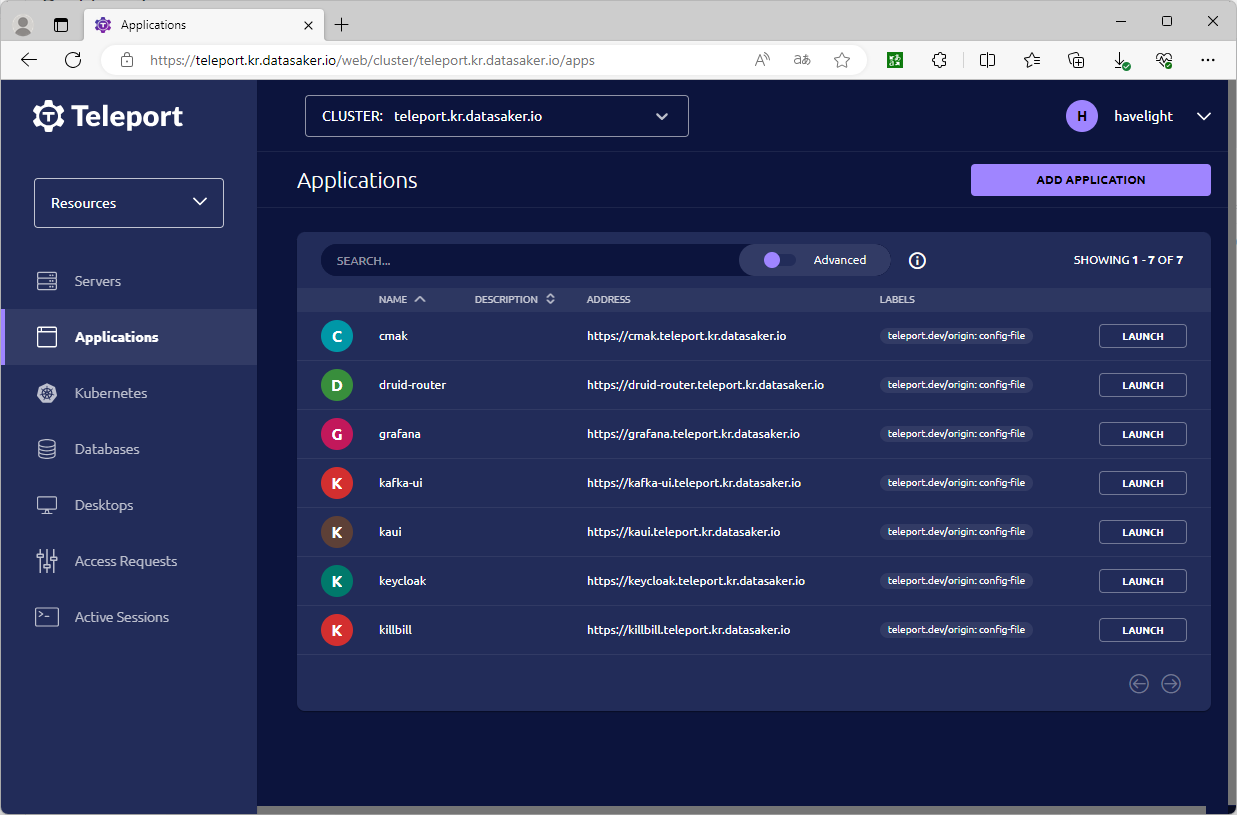
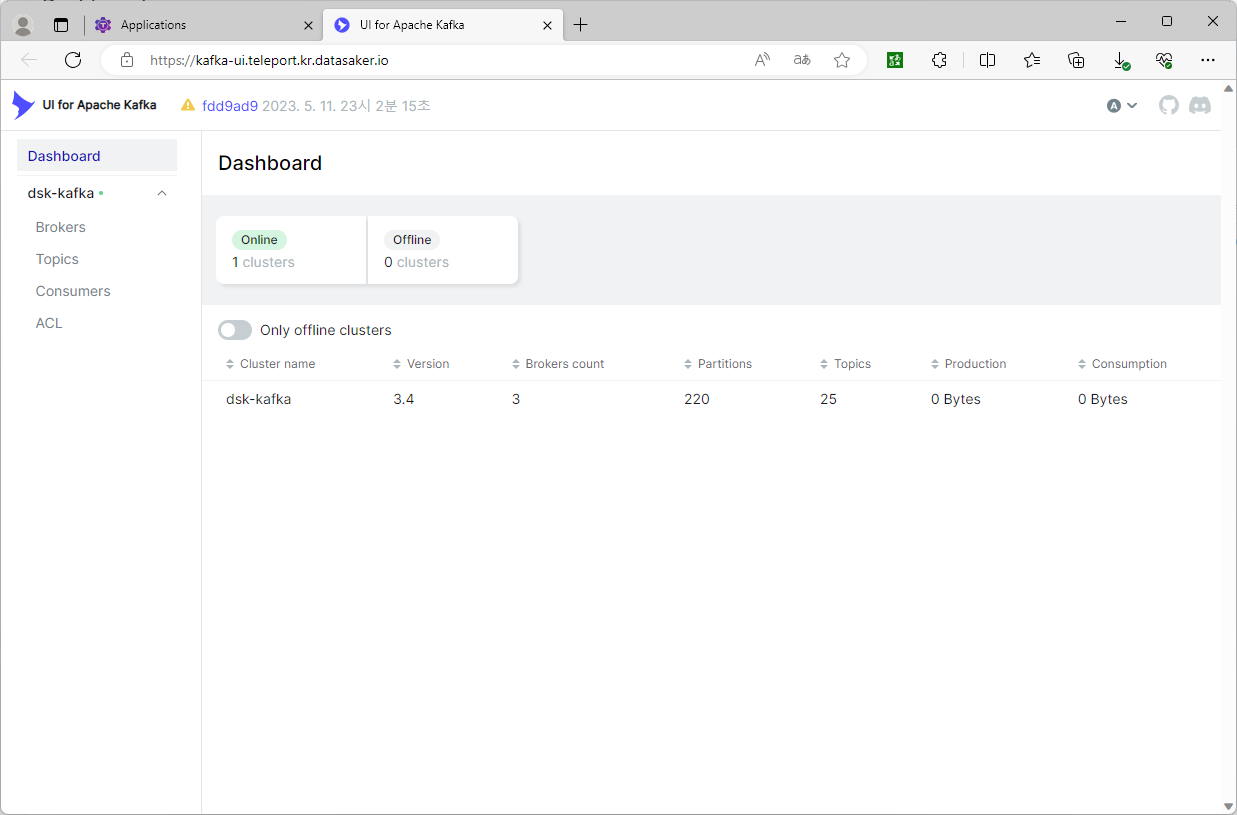
Application 연결
Application web을 teleport를 통해서 특정 domain으로 연결
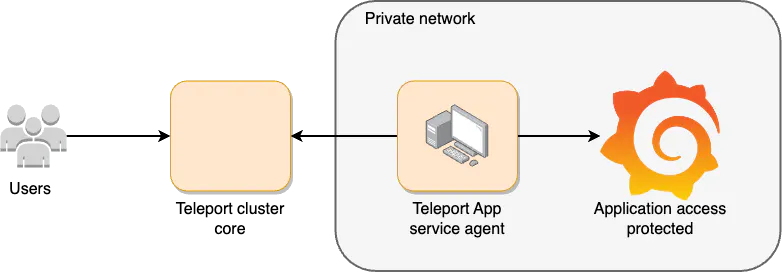
##연결 방법
3024 로 요청이 오기 때문에 방화벽 오픈 필요
# 방화벽 Inbound 오픈 요청
SourceIP : Any
포트
- TCP 443
- TCP 80
- TCP 3023 ~ 3029
Destination IP : 39.115.183.131, 39.115.183.139
사용자 role 생성
kind: role
metadata:
id: 1694589666259084009
name: app-connect
spec:
allow:
app_labels:
'*': '*'
deny:
logins:
- guest
options:
cert_format: standard
create_db_user: false
create_desktop_user: false
desktop_clipboard: true
desktop_directory_sharing: true
enhanced_recording:
- command
- network
forward_agent: false
idp:
saml:
enabled: true
max_session_ttl: 8h0m0s
pin_source_ip: false
port_forwarding: true
record_session:
default: best_effort
desktop: true
ssh_file_copy: true
version: v5
아래의 내용은 devops팀의 구 환경 기준 설정으로 현재는 적용 사항이 아님
현재는 nginx proxy manager로 변경을 하여 아래의 과정 불필요
외부 도메인을 이용하여 proxy를 통해 내부 도메인으로 연결
proxy 설정
# teleport application
use_backend bk_ssl_to_nginx if { req_ssl_sni -i grafana.teleport.kr.datasaker.io }
use_backend bk_teleport_kr_3024 if { req_ssl_sni -i grafana.teleport.kr.datasaker.io }
use_backend bk_ssl_to_nginx if { req_ssl_sni -i cmak.teleport.kr.datasaker.io }
use_backend bk_teleport_kr_3024 if { req_ssl_sni -i cmak.teleport.kr.datasaker.io }
use_backend bk_ssl_to_nginx if { req_ssl_sni -i kaui.teleport.kr.datasaker.io }
use_backend bk_teleport_kr_3024 if { req_ssl_sni -i kaui.teleport.kr.datasaker.io }
use_backend bk_ssl_to_nginx if { req_ssl_sni -i killbill.teleport.kr.datasaker.io }
use_backend bk_teleport_kr_3024 if { req_ssl_sni -i killbill.teleport.kr.datasaker.io }
use_backend bk_ssl_to_nginx if { req_ssl_sni -i kafka-ui.teleport.kr.datasaker.io }
use_backend bk_teleport_kr_3024 if { req_ssl_sni -i kafka-ui.teleport.kr.datasaker.io }
use_backend bk_ssl_to_nginx if { req_ssl_sni -i keycloak.teleport.kr.datasaker.io }
use_backend bk_teleport_kr_3024 if { req_ssl_sni -i keycloak.teleport.kr.datasaker.io }
use_backend bk_ssl_to_nginx if { req_ssl_sni -i druid-router.teleport.kr.datasaker.io }
use_backend bk_teleport_kr_3024 if { req_ssl_sni -i druid-router.teleport.kr.datasaker.io }
# ssl > nginx
backend bk_ssl_to_nginx
mode tcp
balance roundrobin
option ssl-hello-chk
server web01 127.0.0.1:8443 check inter 2s
# 3024 > teleport proxy
listen 3024_in
bind *:3024
mode tcp
balance roundrobin
use_backend bk_teleport_kr_3024
backend bk_teleport_kr_3024
mode tcp
balance roundrobin
server teleport_server_kr_3124 10.10.43.240:30813 check
```
2. 인증서 발급
```plain
domains=('grafana' 'cmak' 'killbill' 'kafka-ui' 'keycloak' 'druid-router')
for domain in ${domains[@]}
do
"certbot certonly --standalone -d ${domain}.teleport.kr.datasaker.io --non-interactive --agree-tos --email havelight@ex-em.com --http-01-port=8899 -v"
done
```
3. nginx 설정
```shell
rp-grafana-teleport-kr.conf
rp-kaui-teleport-kr.conf
rp-kafka-ui-teleport-kr.conf
rp-keycloak-teleport-kr.conf
rp-cmak-teleport-kr.conf
rp-druid-router-teleport-kr.conf
rp-killbill-teleport-kr.conf
```
2. agent 설치
\- token 발급
```shell
tsh login --proxy teleport.kr.dataskaer.io --user [계정명]
tctl tokens add --type=app
- helm chart
helm repo add teleport https://charts.releases.teleport.dev
helm repo update
helm pull teleport/teleport-kube-agent --untar
- prod_values.yaml
authToken: "[발급받은 token]"
proxyAddr: "teleport.kr.datasaker.io:443"
roles: "app" #(any of: kube,db,app)
apps:
- name: cmak
uri: http://cmak.dsk-middle.svc.cluster.local:9000
- name: kaui
uri: http://dsk-kaui.dsk-middle.svc.cluster.local:8080
- name: killbill
uri: http://dsk-killbill.dsk-middle.svc.cluster.local:8080/api.html
- name: kafka-ui
uri: http://kafka-ui.dsk-middle.svc.cluster.local
- name: keycloak
uri: http://keycloak.dsk-middle.svc.cluster.local
- name: druid-router
uri: http://druid-router.dsk-middle.svc.cluster.local:8888/unified-console.html
storage:
enabled: true
storageClassName: ""
requests: 128Mi
- helm install
helm -n teleport-agent install teleport-agent . -f prod_values.yaml --create-namespace
- 확인
# kubectl -n teleport-agent get all
NAME READY STATUS RESTARTS AGE
pod/teleport-agent-0 1/1 Running 0 141m
NAME READY AGE
statefulset.apps/teleport-agent 1/1 22h
# kubectl -n teleport-agent get cm teleport-agent -o yaml
apiVersion: v1
data:
teleport.yaml: |
app_service:
apps:
- name: cmak
uri: http://cmak.dsk-middle.svc.cluster.local:9000
- name: kaui
uri: http://dsk-kaui.dsk-middle.svc.cluster.local:8080
- name: killbill
uri: http://dsk-killbill.dsk-middle.svc.cluster.local:8080/api.html
- name: kafka-ui
uri: http://kafka-ui.dsk-middle.svc.cluster.local
- name: keycloak
uri: http://keycloak.dsk-middle.svc.cluster.local
- name: druid-router
uri: http://druid-router.dsk-middle.svc.cluster.local:8888/unified-console.html
enabled: true
auth_service:
enabled: false
db_service:
enabled: false
kubernetes_service:
enabled: false
proxy_service:
enabled: false
ssh_service:
enabled: false
teleport:
join_params:
method: token
token_name: /etc/teleport-secrets/auth-token
log:
format:
extra_fields:
- timestamp
- level
- component
- caller
output: text
output: stderr
severity: INFO
proxy_server: teleport.kr.datasaker.io:443
version: v3
kind: ConfigMap
metadata:
annotations:
meta.helm.sh/release-name: teleport-agent
meta.helm.sh/release-namespace: teleport-agent
creationTimestamp: "2023-09-13T07:15:32Z"
labels:
app.kubernetes.io/managed-by: Helm
name: teleport-agent
namespace: teleport-agent
resourceVersion: "144094053"
uid: 57c4e43e-88e5-42fd-abba-bccecbdab0e1